Get to know this modus operandi used by scammers to get to your data
Phishing is the most prevalent cyber crime we have today. Around 83% of businesses experiencing phishing attacks annually. With cyber criminals constantly looking for ways to bait in more victims, it is best to know what we are up against.
Email phishing attacks are still going around. However, with increased awareness of their presence and efficient anti-virus, they have become less effective over time. As such, threat actors are adapting new ways to catch their victims that bypass both the user and security solutions in place.
Currently, another go-to technique is by using photos to lure in their victims. Using the images to hide the malicious URLs, hackers are able to bypass filters from email services like Outlook and Gmail designed to protect their users from phishing.
They use very large and very convincing promotional photos to entice customers into clicking the photos. This usually comes in the form of a one-time deal, best-offer, limited-time promo only banner that is too good to miss. The promos are usually made like what you get from famous retail brands and services like BestBuy, Amazon and even your Anti-Virus software provider. However, once you click on these photos it will redirect you to a legit-looking page, albeit a fake one, which will harvest your information like username and password.

Photo Phishing Attacks
Warning Signs of these Phishing Attacks
Sure, we know it’s hard to pass up on a great deal. But is it worth it in exchange for your business information? You wouldn’t think so either.
So what should we look out for when getting promotional photos?
Random Emails are Usually Phishing Attacks
First, getting email from random senders is already a major red flag. If it is something you are not expecting. Or it came from an unknown person or company, chances are, it is a scam.
Second, check for the greeting. Yes, if the sender knows you, the email should start with greeting you by name and not something generic. Usually, reading a letter from someone you know or know you would give hints about where and how you are connected. For example, they may mention an event or an occasion where you met. Or maybe a campaign that you and the sender worked on together.
Very Enticing and Time-Sensitive Offers
Yes, we love a great offer as much as the next person. However, think first if the offer is reasonable or justifiable. Businesses will not give anything free if they are not getting anything from you to compensate for the capital invested. Most of the time, promos have a fine print that you can check for added details regarding the offer.
Likewise, ads that pressure you to take action in a very small amount of time are also suspicious. This is especially true if there is no prior warning. Businesses with a limited time offer would usually advertise the schedule prior to the actual event to maximize response from customers.
You can also check their official websites and stores to verify the promos. Companies offering amazing deals would advertise this everywhere, or at least on their official websites. If it is not anywhere else but your inbox, that is a red flag. Remember, if it is too good to be true, then it probably isn’t.
Typographical Errors
Businesses who send out promotional deals to customers usually have more than one person looking into the ad material. Hence, the chance of having a typographical error is very slim, especially not multiple errors in one photo. Sure, no system is perfect so maybe one or two misspells make it through the final layout. But if it’s too much for comfort, you might as well steer clear.
Logos and Brands
Logos and branding is a company’s identity. If you get an email from a business that seems off, it probably is a scam. You may not be able to put a finger on the detail that changed but usually a slight change in color or font would make it seem unnatural especially if you see the logo often. Recheck the company’s official website and play “spot the difference” and you will eventually see the hacker’s handiwork.
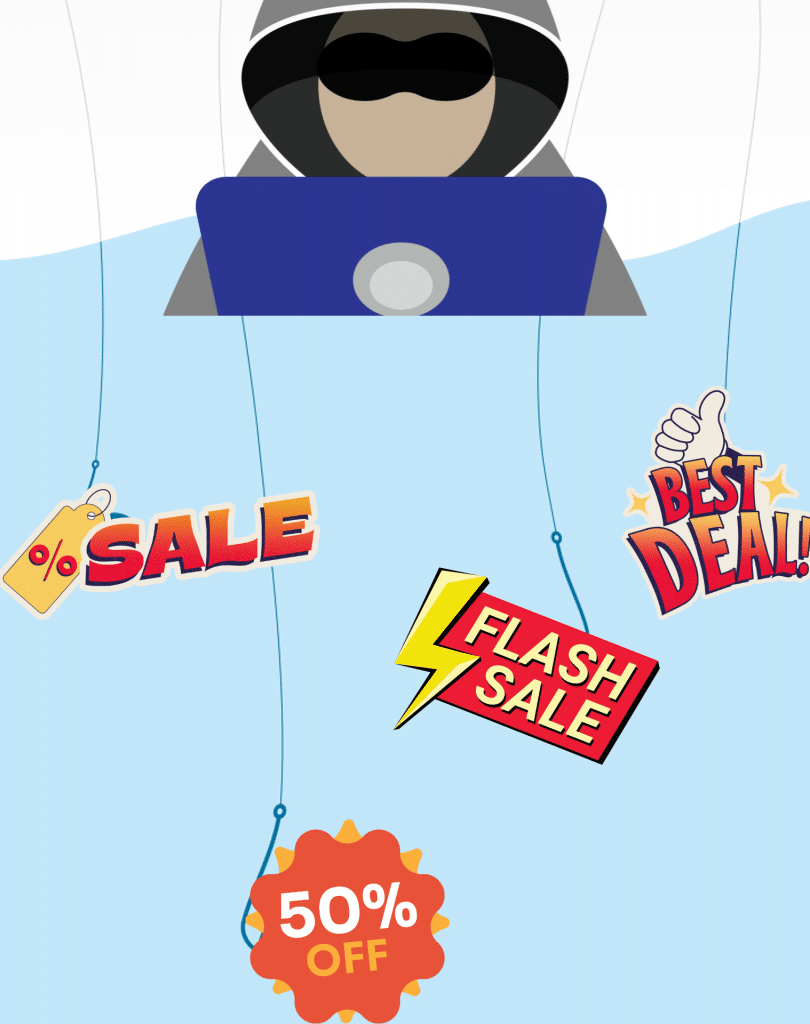
Photo Phishing Attack
Keep Away from these Phishing Attacks?
So how do we keep ourselves from being victims of these phishing scams?
Education and Training About Phishing Attacks
Knowing what you and your team are up against is always the first line of defense. Make sure to update your staff regarding scams that are going around. Should you happen to receive a suspicious looking photo in your email, make sure to give your employees a heads-up about it so they can avoid it as well.
You can schedule in-house or online training for you and your team to keep you updated on tech news and cyber crime prevention. You can reach out to us for more details!
Update Software
Make use of software updates to ensure you and your business system are protected. Outdated software usually means hackers have already bypassed their filters and security measures. Software updates mean improved versions and would already have protection against new threats and cover up any weak spots that hackers can exploit.
Strong Passwords
Generic passwords, although convenient, are unfortunately unsafe. A strong and unique password will protect you from unwanted and unauthorized access. Different passwords for multiple systems are also encouraged so that in the event that one password leaks out, other accounts are still protected. Use a password manager to help make things easier for you but not for the cyber criminals.
Use MFA’s
Add an extra layer of security to your business system by enabling Multi-Factor Authentication (MFAs). This would require your staff to verify their identity on top of the passwords. It may use text messages or biometrics. If you are unsure about this, you can get in touch with us, and we can set this up for you.
Back-up Files
Lastly, always back up your files. This is in case a major attack does happen to you. Your back-up files will help you stay afloat despite the data compromise. Some data may get lost in the process but at the very least, you will not start back from scratch.
Need help against these phishing attacks?
Threat actors are always trying new ways to get their hands on your information or spread malware to serve their purpose. Make sure to always be a few steps ahead to protect your business from these scammers. Get in touch with us now so we can discuss the details.
