No business wants to suffer a data breach, but it’s difficult to completely avoid them. Approximately 83% of organizations have experienced more than one breach, according to the IBM Security 2022 Cost of a Data Breach Report. Unfortunately, with the rise in data breaches, it’s possible that your personal information has been exposed in recent breaches.
Breaches have multiple consequences for businesses. The immediate cost of remediating the breach, lost productivity and business, lost customer trust, and potential legal costs all contribute to the overall impact of a breach.
In 2022, the cost of a data breach rose to $4.35 million globally and $9.44 million in the U.S., with Canada having an average cost of $5.64 million, according to the IBM Security report. Smaller companies may have lower costs, but breaches can be more devastating due to limited resources to offset the costs. It’s estimated that 60% of small companies go out of business within six months of a breach.
However, businesses can reduce the damage of a cyberattack by implementing proven cybersecurity practices.
How to Minimize Data Breach Impact?
All the following statistics come from the IBM Security report.
Adopt a Hybrid Cloud Model
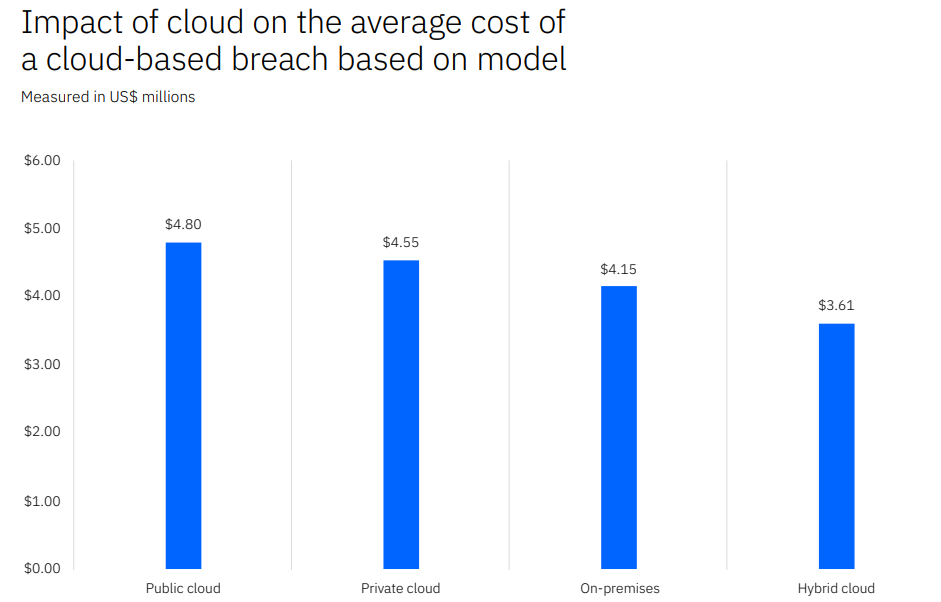
Many businesses rely on the cloud for data storage and operations, but research indicates that 45% of data breaches occur in the cloud. However, not all cloud solutions are equally secure. Breaches in public clouds tend to be more costly than those in hybrid clouds.
A hybrid cloud model refers to a combination of public and private cloud environments, where some data and processes are stored in the public cloud and others in a private cloud. It provides the benefits of scalability and cost-effectiveness offered by public clouds, while maintaining control over sensitive information through the use of a private cloud. This approach has been proven to be more secure than private clouds and offers a better balance between security and accessibility, allowing businesses to focus on their core operations with peace of mind.
Develop and Rehearse an Incident Response Plan
Creating an incident response (IR) plan is essential for organizations of all sizes. This plan is a set of guidelines for employees to follow in the event of various cybersecurity incidents.
For instance, in case of a ransomware attack, the initial step should be to isolate the affected device. Once the affected device has been isolated, the next step would be to assess the extent of the attack and determine the best course of action. This could involve contacting a cybersecurity specialist or activating the organization’s incident response team, who would then follow the guidelines laid out in the IR plan. The team would need to determine the origin of the attack, the type of ransomware being used, and the extent to which the organization’s systems and data have been impacted.
It is important to determine whether to pay the ransom or not. If the organization decides not to pay the ransom, it must have a solid backup and disaster recovery plan in place to restore the data and systems.
A well-rehearsed IR plan can quicken and enhance the response to a security crisis. Regularly practicing the IR plan scenarios with all relevant personnel helps to identify areas that need improvement and reinforces the proper protocols to follow in a crisis situation.
An incident response plan can significantly lower the cost of a data breach. On average, it reduces the cost by $2.66 million per incident.
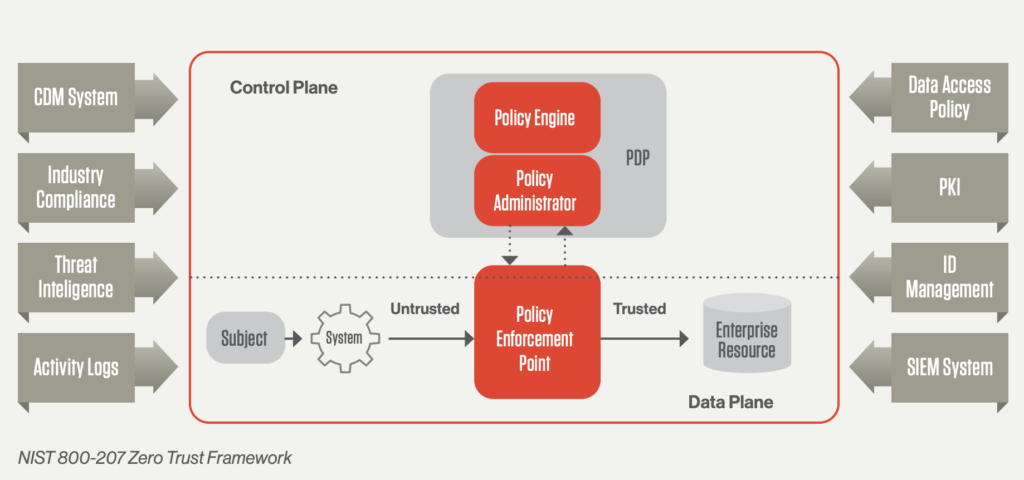
Implement a Zero Trust Security Model
A zero trust security approach encompasses a set of security measures that work cohesively to secure a network. Some of these measures include: Multi-factor authentication, Application whitelisting, Contextual user authentication.
Unfortunately, many critical infrastructure organizations have yet to implement this approach, with 79% still not adopting zero trust. Implementing zero trust security can significantly reduce the costs associated with data breaches, as organizations without these tactics typically incur $1 million more per breach.
Embrace Security Tools with AI and Automation
The choice of security tools can greatly impact the expenses incurred during a data breach. Utilizing tools that utilize security AI and automation has been shown to yield the most significant cost savings. Incorporating these solutions has been found to lower data breach expenses by 65.2%. Examples of such solutions include advanced threat protection (ATP) and applications that detect and respond to threats automatically.
Incorporating security tools with AI and automation not only results in cost savings but also helps organizations stay ahead of the constantly evolving threat landscape. With AI algorithms capable of detecting patterns and anomalies in real-time, organizations are able to quickly respond to potential security incidents. These tools also minimize the risk of human error, ensuring that security systems run smoothly and efficiently by automating time-consuming and repetitive tasks.
Steps to Enhance Your Cybersecurity Defense
Enhancing your cybersecurity defense can be done by implementing best practices gradually. To get started, it is recommended to collaborate with a reliable IT service provider and develop a roadmap that prioritizes quick wins and long-term goals.
One such “quick win” could be implementing multi-factor authentication, which is a low-cost and effective measure to reduce the risk of a cloud breach. On the other hand, a longer-term project could be creating a well-rehearsed incident response plan and regularly conducting drills to ensure its smooth functioning.
Get Expert Support for Improved Security and Reduced Risk
Partnering with a trusted IT service provider can ease your security concerns. With the increasing frequency of data breaches, it is more important than ever to have a robust cybersecurity strategy in place. By partnering with a trusted IT service provider, you can ensure that your organization’s sensitive information is protected. EB Solution has more than a decade of experience helping small and medium-sized businesses with their cybersecurity. Our experts can help you create a customized cybersecurity roadmap that fits your specific needs and gives you peace of mind. Don’t wait until it’s too late, contact us today to schedule a discussion.